FakeCall Vishing Malware: Comprehensive Guide to Detection, Removal, and Prevention
FakeCall Vishing Malware is a persistent threat in the cybersecurity landscape, combining traditional phishing techniques with a malicious app to…
Cybro AirDrop Scam: Protect Your Device with This Comprehensive Removal Guide
In the digital age, scams and malware are constantly evolving to deceive unsuspecting users. One recent threat that’s been circulating…
Axie Infinity Claim Scam: An NFT Ruse with Costly Consequences
In the rapidly evolving world of cryptocurrency, scams have become alarmingly prevalent, targeting both novice and experienced users alike. One…
MetaMask Wallet Verification Scam: A Complete Guide to Recognizing, Removing, and Preventing Phishing Threats
Phishing scams, like the recent MetaMask Wallet Verification scam, have become increasingly sophisticated, specifically targeting online financial assets. These scams…
Understanding PUPs: The Threat of Edge Update Malware
In today’s digital age, users often encounter various forms of malware that threaten their online experience. One of the more…
“Capital One Dispute Claim Processed” Scam Email
Phishing scams are fraudulent attempts to steal sensitive information by masquerading as legitimate entities. A prevalent example is the "Capital…
Camelot Lottery Solutions Phishing Scam
Phishing scams like the Camelot Lottery Solutions email aim to deceive individuals by promising large compensation payouts. This particular scam…
Aave Check Eligibility Scam: A New Cyber Threat
The Aave Check Eligibility scam is the latest cyber threat targeting unsuspecting users. Disguised as a legitimate notification or offer,…
American Express Card Temporarily Flagged Malware
Cyber threats have become increasingly sophisticated, targeting individuals and organizations with malicious intent. One such alarming threat is the American…
Sonic AirDrop Malware: Actions, Consequences, and Removal Guide
Cyber threats continue to evolve, posing significant risks to users worldwide. One such threat is the Sonic AirDrop malware, a…
Aruba IT Email Scam: A Comprehensive Malware Removal Guide
Phishing scams are deceptive tactics used by cybercriminals to manipulate individuals into revealing sensitive information, such as passwords, credit card…
Nodeainetwork Scam: Actions, Consequences, and Prevention
Cyber threats are increasingly getting more sophisticated, and one of the most concerning threats currently is the Nodeainetwork scam. This…
Soneium Registration Scam: Threats, Actions, and Removal Guide
One nototrious cyber threat is the Soneium Registration Scam, which aims to deceive users into providing personal information and payment…
BlockDag Presale Scam: A Rising Cyber Threat
In the ever-evolving landscape of cyber threats, scams targeting cryptocurrency investors have become increasingly sophisticated and deceptive. One such threat…
Your Netflix Subscription is Expiring Soon Email Scam: A Comprehensive Guide
In the digital age, phishing scams have become a prevalent and sophisticated threat to users worldwide. These scams often take…
Wallet Guard Scam: Threats, Actions, and Prevention
In an age where online transactions have become the norm, cybercriminals are continuously devising more sophisticated scams to exploit unsuspecting…
GetFit Mining Scam: Removal Guide and Prevention Tips
GetFit Mining is a deceptive scam that masquerades as a legitimate cryptocurrency mining application but operates to exploit users by…
Moving Funds to Your Account Email Scam
Phishing scams have become increasingly prevalent, targeting unsuspecting individuals through deceptive emails designed to steal sensitive information or compromise systems.…
Valorant Skin Giveaway Scam: Understanding the Threat and How to Protect Yourself
In recent months, the gaming community has witnessed an alarming rise in cyber threats, particularly in the form of scams…
AddonUp Extension Virus: Understanding the Threat and How to Remove It
Browser extensions have become a common vector for malware distribution. One such threat is the AddonUp Extension virus, which infiltrates…
Beware of the Fifth Third Bank Phishing Scam: A Comprehensive Guide
Phishing scams are deceitful tactics used by cybercriminals to trick individuals into providing sensitive information, such as passwords, credit card…
Trust Wallet Security Alert Email Scam: Understanding Phishing Scams
Phishing scams have become increasingly sophisticated and prevalent. These scams often take the form of fraudulent emails or messages that…
Bank of Scotland Email Scam: A Comprehensive Guide
Phishing scams are deceitful attempts to trick individuals into revealing sensitive information, such as usernames, passwords, credit card numbers, and…
W.J. Daniel & Co., Ltd. Email Scam: A Guide to Understanding and Combatting Phishing Threats
Phishing scams have become increasingly prevalent in today's digital landscape, where malicious actors attempt to deceive individuals into revealing personal…
Google Syncing Passkeys: A Potential Cybersecurity Threat
Google’s recent initiative to sync passkeys across desktop and Android devices has brought both convenience and heightened security concerns. While…
Claim Aerodrome Rewards Scam: Understanding the Threat and Protecting Yourself
Scams and cyber threats have become increasingly sophisticated, often disguised as legitimate offers to entice unsuspecting victims. One such threat…
SmartColor Password Expiry Email Scam: What You Need to Know and How to Remove It
Phishing scams have become an increasing threat in today's digital landscape, and email phishing remains one of the most effective…
Dzentime Virus: A Complete Removal Guide
Cyber threats continue to evolve, becoming more dangerous and sophisticated with each passing day. One such growing threat is the…
Claim Eigen Scam: Detailed Overview and Removal Guide
The Claim Eigen scam is a deceptive and potentially harmful cyber threat that has been making rounds on the internet.…
“Confirm That This Is Your Valid Email Address” Phishing Scam
Phishing scams are a pervasive threat in today’s digital landscape, designed to deceive individuals into revealing sensitive information or installing…
“Website Suspension in Progress” Phishing Scam: Fighting Email Scams
Phishing scams are deceptive tactics used by cybercriminals to trick individuals into divulging sensitive information, such as usernames, passwords, or…
“I’ve Got Access to Your Smartphone” Email Scam: A Comprehensive Guide to Protecting Yourself
Phishing scams are a constant threat in today’s digital world, evolving with each new tactic to deceive unsuspecting victims. One…
Missed Call Voicemail Alert Scam: A Phishing Threat to Watch Out For
Phishing scams have become increasingly sophisticated, using clever tactics to deceive users into divulging sensitive information or installing harmful software.…
Rothschild Foundation Email Scam: A Dangerous Phishing Threat and How to Protect Yourself
Phishing scams have become an increasingly common threat, targeting individuals and businesses alike. These deceptive schemes typically present themselves as…
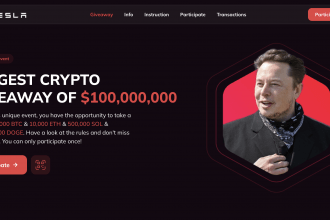
Elon Musk X Donald Trump Crypto Giveaway Scam
Cybercriminals are constantly evolving their tactics, creating scams that prey on users' trust in high-profile figures. One such scheme is…
“Your Device Is at Risk” Pop-up Scam on Mac: How to Remove It and Protect Your System
The "Your Device Is at Risk" pop-up scam is one of the many deceptive alerts targeting Mac users, designed to…
Email Resource Alert Triggered Email Scam: Understanding the Threat and How to Protect Yourself
Phishing scams continue to plague the digital world, exploiting unsuspecting individuals and their systems. One such malicious tactic is the…
“Removing Useless Files Is Advised” Pop-Up Scam
Pop-up scams are deceptive messages or alerts that appear unexpectedly on a user's screen, often during web browsing. These scams…
“Email Suspension at Server Database”: Beware of the cPanel – Server Glitch Phishing Scam
Phishing is a form of cyber-attack where malicious actors impersonate legitimate entities to deceive individuals into revealing sensitive information or…
“Payment Approved by International Authorities” Phishing Scam: Avoiding Phishing Attacks
Phishing scams are deceptive attempts to acquire sensitive information by masquerading as a trustworthy entity. These scams typically come in…
Beware of the ‘New Order from Start Group S.R.L’ Deception: How the Start Group S.R.L Email Scam Targets You
Phishing scams are one of the most common forms of online fraud today. Typically executed through email, phishing scams deceive…
“More Convenient Way” Email Scam
Phishing scams have evolved significantly over the years, becoming increasingly sophisticated and difficult to identify. These scams often masquerade as…
Claim Base Dawgz Scam Pop-Up
Pop-up scams are deceptive online threats designed to trick users into divulging personal information or downloading malicious software. These scams…
Avast Scan Phishing Scams
Phishing scams are a prevalent and dangerous form of cyberattack where malicious actors deceive individuals into providing sensitive information, such…
“Join Our Great Illuminati” Email Phishing Scam
Phishing scams are a significant threat in today’s digital age, where malicious actors exploit deceptive tactics to trick individuals into…
MOG Coin Scam: A Comprehensive Guide to Understanding and Removing the Threat
The digital age has brought with it a surge in cyber threats that exploit the growing popularity of cryptocurrencies. One…
Cromex Agent AB Pop-Up Scam: How to Identify and Remove Malware Deployed from Scams
Pop-up scams are particularly dangerous because they exploit the trust users place in their browsers or operating systems. They often…
The Irrevocable Payment Order Email Scam
Email scams are fraudulent schemes where attackers use deceptive messages to trick individuals into revealing sensitive information, downloading malware, or…
TotalEnergies Email Scam: Understanding Email Fraud
Phishing scams are deceptive tactics used by cybercriminals to obtain sensitive information, such as usernames, passwords, and financial details, by…
Chromex Agent AB Pop-Up Scam: Battling Fraudulent Ads
In the digital age, pop-up scams have become a prevalent threat, often designed to deceive and exploit unsuspecting users. These…