“Safety Warning” Scam
Online scams are becoming increasingly sophisticated, preying on users' fears to manipulate them into falling for fraudulent schemes. One such…
“Failed To Remove Viruses” Scam: A Detailed Guide to Protect Your Device
The "Failed To Remove Viruses" scam is a fraudulent pop-up that deceives users by falsely claiming their device is infected…
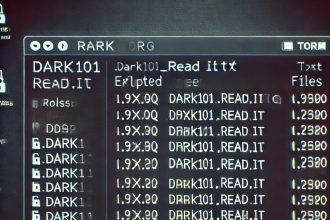
Dark 101 Ransomware: A Detailed Threat Analysis and Removal Guide
Dark 101 is a ransomware-type malware based on the Chaos framework, recently discovered during a routine inspection of new submissions…
ClickFix Malware: Understanding and Removing the Threat
ClickFix is a deceptive malware campaign that tricks users into executing malicious commands under the guise of resolving errors or…
CatLogs Malware: Analysis and Removal Guide
CatLogs is a sophisticated stealer-type malware that has been creating significant havoc in the cybersecurity space. This malicious program is…
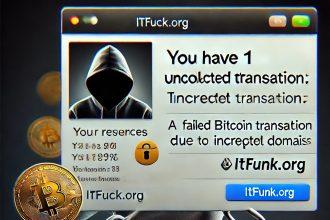
“You Have 1 Uncollected Transaction” Scam: Understanding and Avoiding This Threat
Overview of the Scam The "You Have 1 Uncollected Transaction" scam is a phishing scam designed to deceive unsuspecting users…
Bigsupersweepstakes.com: A Guide to Understanding and Eliminating the Threat
In the vast digital landscape, malicious entities like Bigsupersweepstakes.com emerge to exploit unsuspecting users. This rogue website employs manipulative tactics,…
“Salary Review” Email Scam
The “Salary Review” email scam is an elaborate phishing campaign that masquerades as a notification from an organization’s Human Resources…
Bright_setup.exe: Understanding the Threat and Removal Guide
Bright_setup.exe is a file associated with Bright VPN, a free virtual private network service provided by Bright Data. While Bright…
Altrousik Service: Removal and Prevention
Altrousik Service is a malicious browser hijacker that has been causing significant disruptions for users by altering browser settings, redirecting…
Networkcontrol.co[.]in Ads: Analysis and Removal
In today’s digital landscape, online threats are evolving, targeting unsuspecting users through various techniques. Networkcontrol.coin is one such deceptive page…
“Classified Documents” Email Scam
Overview of the Threat The "Classified Documents" email scam is a sophisticated phishing attack designed to trick recipients into providing…
Mania Crypter Ransomware: Understanding and Removing the Threat
Mania Crypter is a dangerous ransomware variant based on the infamous LockBit Black. This malware encrypts files, appends a random…
Kowi SApp Threat Removal
What is Kowi SApp? Kowi SApp is a dangerous and unwanted application flagged by multiple security vendors. Deceptively distributed, it…
innok Ransomware: Analyzing the Threat and How to Remove It
Ransomware remains one of the most pervasive cyber threats, and innok ransomware is no exception. This malicious software encrypts victims’…
Cash-searcher[.]com
Cash-searchercom is a deceptive website designed to manipulate users into subscribing to its notifications or engaging with fraudulent schemes. Threat…
“Donation From Frances and Patrick Connolly” Email Scam
In the evolving world of cyber threats, scammers continue to leverage creative methods to deceive individuals into sharing sensitive information…
What Is Baraag.net? Everything You Need to Know About This Risky Platform
Baraag.net is a microblogging platform within the Mastodon network. It caters to a niche audience of artists and enthusiasts of…
Clearnview Pop-up – Should You Be Worried?
The Clearnview pop-up issue refers to security alerts triggered by antivirus programs, such as Norton, warning users about attempts to…
behque[.]click Rogue Website
The internet is rife with malicious websites aiming to deceive unsuspecting users, and one such entity is the behqueclick rogue…
“$OBT Airdrop” Scam: Protect Your Cryptocurrency Wallets
Cryptocurrency scams continue to evolve, and the fake "$OBT Airdrop" is one of the latest schemes targeting unsuspecting investors. This…
euopue[.]click
In the ever-evolving landscape of cybersecurity threats, deceptive websites such as euopueclick have emerged as significant dangers to users. This…
Flightsettle[.]site
Flightsettlesite is a malicious website designed to deceive users into granting permission for intrusive push notifications. These notifications are used…
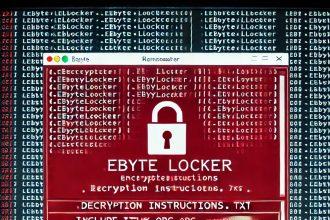
EByte Locker Ransomware: A Detailed Guide to Understanding, Removing, and Preventing This Threat
What Is EByte Locker Ransomware? EByte Locker is a malicious ransomware strain based on the Prince ransomware family. It encrypts…
Traw Dapp Threat
Traw Dapp is classified as a malicious application by numerous security vendors, and its functionality primarily revolves around delivering dangerous…
Spring Ransomware: Understanding and Removal
Spring ransomware is a malicious program based on the CONTI ransomware family, designed to encrypt files and demand a ransom…
PNGPlug Malware: A Silent Threat in Cybersecurity
PNGPlug is a sophisticated malware loader actively used in attacks targeting Chinese-speaking regions, including Hong Kong, Taiwan, and mainland China.…
The-Prize-Stash.com: Understanding and Removing This Threat
The-prize-stash.com is a fraudulent and malicious website designed to lure unsuspecting users into clicking on deceptive links and pop-ups under…
Is Upgrader.exe Dangerous? Identifying and Removing the Threat
The "Upgrader.exe" file has been raising suspicions among users due to its potential connection to malware. While some instances of…
Fake “Claim Obol” Website
The rise of cryptocurrency has brought both opportunities and risks. Among these risks are malicious scams that target unsuspecting users,…
“Bittrex Inc Bankruptcy Notice” Scam: Protect Yourself from Crypto Drainers
Cybercriminals are increasingly leveraging sophisticated tactics to deceive unsuspecting victims, and the "Bittrex Inc Bankruptcy Notice" email is a prime…
“Capital One – Unusual Spending Activities Detected” Email Scam
The “Capital One - Unusual Spending Activities Detected” scam email is part of a phishing campaign targeting unsuspecting individuals. Disguised…
“Chase Account Temporarily Restricted” Phishing Email Scam
Overview of the Threat The "Chase Account Temporarily Restricted" email scam is a deceptive phishing campaign designed to steal sensitive…
Protect Your Cryptocurrency: Jupiverse Wallet Connection Scam Exposed
The world of cryptocurrency has brought immense opportunities, but it also opens doors to sophisticated scams. One such alarming threat…
VirTool:PowerShell/MaleficAms.L
Key Details About the Threat AttributeDetailsThreat TypeTrojan HorseDetection NamesVirTool:PowerShell/MaleficAms.LSymptoms of Infection- Slowed computer performance- Unexpected pop-ups or banner ads- Increased…
Trojan:Win32/Amadey!rfn – A Stealthy Trojan Threat
Trojan:Win32/Amadey!rfn is a heuristic detection for a Trojan horse that exhibits malicious behavior capable of compromising sensitive user data, installing…
Bpant Ransomware: Understanding and Mitigating the Threat
If your files suddenly have the extension .Bpant and a ransom note demands Bitcoin payments, your system is likely infected…
Searchinstyle.com Browser Hijacker: Removal and Prevention
Searchinstyle.com is a browser hijacker and a potentially unwanted application (PUA) that infiltrates systems through bundled software installations or deceptive…
Trojan.MisplacedLegit.AutoIt Malware: A Detailed Guide to Understanding and Removal
Trojan.MisplacedLegit.AutoIt is a Trojan malware threat often linked to the misuse of the AutoIt scripting language, a legitimate tool for…
Disoaq App: Understanding the Threat and How to Remove It Safely
Potentially Unwanted Applications (PUAs) such as Disoaq App can have hazardous effects on systems and user privacy. This article delves…
“Sign-in Attempt Was Blocked” Email Phishing Scam
Cybersecurity threats have grown increasingly sophisticated, and phishing scams like the "Sign-in Attempt Was Blocked" email are prime examples of…
D0glun Ransomware – Threat Analysis and Removal Guide
Ransomware continues to evolve, with new threats like D0glun targeting unsuspecting users. This ransomware-type virus encrypts victims' files and demands…
Removing InvisibleFerret Malware
InvisibleFerret is a Python-based backdoor malware associated with North Korean threat actors. It is a highly sophisticated tool used to…
Clone Ransomware: Understanding the Threat and How to Remove It Effectively
Clone ransomware is a member of the notorious Dharma ransomware family, identified during a routine analysis of malicious submissions on…
Chatsixgirl.com Redirect Virus: Detailed Removal Guide and Prevention Tips
Chatsixgirl.com is a harmful and deceptive website categorized as a potentially unwanted program (PUP). Though it may appear to offer…
Helldown Ransomware Removal
Helldown is an aggressive ransomware strain first identified in August 2024. It operates using double extortion tactics, encrypting victims’ data…
What Is Steam.aeonsecho.com?
Steam.aeonsecho.com is a deceptive website posing as a portal for an online adult game on Steam. It is designed to…
“Docker” Will Damage Your Computer Mac Virus
The “Docker” Will Damage Your Computer Mac virus is an annoying and potentially harmful software that targets Mac users. Though…
Beware of the Fake “DApp Rectification” Website: Protect Your Cryptocurrency
The world of cryptocurrency, with its decentralized structure and lucrative opportunities, attracts not only investors but also cybercriminals. Among the…
“Fine For Visiting Pornographic Websites” Scam
The "Fine For Visiting Pornographic Websites" scam is a deceptive scheme targeting unsuspecting users with fake fines for alleged law…