Clearnview Pop-up – Should You Be Worried?
The Clearnview pop-up issue refers to security alerts triggered by antivirus programs, such as Norton, warning users about attempts to…
behque[.]click Rogue Website
The internet is rife with malicious websites aiming to deceive unsuspecting users, and one such entity is the behqueclick rogue…
Flightsettle[.]site
Flightsettlesite is a malicious website designed to deceive users into granting permission for intrusive push notifications. These notifications are used…
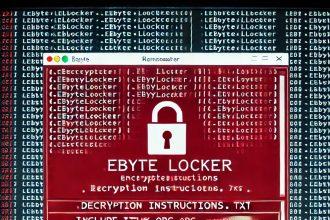
EByte Locker Ransomware: A Detailed Guide to Understanding, Removing, and Preventing This Threat
What Is EByte Locker Ransomware? EByte Locker is a malicious ransomware strain based on the Prince ransomware family. It encrypts…
Traw Dapp Threat
Traw Dapp is classified as a malicious application by numerous security vendors, and its functionality primarily revolves around delivering dangerous…
Spring Ransomware: Understanding and Removal
Spring ransomware is a malicious program based on the CONTI ransomware family, designed to encrypt files and demand a ransom…
PNGPlug Malware: A Silent Threat in Cybersecurity
PNGPlug is a sophisticated malware loader actively used in attacks targeting Chinese-speaking regions, including Hong Kong, Taiwan, and mainland China.…
Is Upgrader.exe Dangerous? Identifying and Removing the Threat
The "Upgrader.exe" file has been raising suspicions among users due to its potential connection to malware. While some instances of…
Protect Your Cryptocurrency: Jupiverse Wallet Connection Scam Exposed
The world of cryptocurrency has brought immense opportunities, but it also opens doors to sophisticated scams. One such alarming threat…
VirTool:PowerShell/MaleficAms.L
Key Details About the Threat AttributeDetailsThreat TypeTrojan HorseDetection NamesVirTool:PowerShell/MaleficAms.LSymptoms of Infection- Slowed computer performance- Unexpected pop-ups or banner ads- Increased…
Trojan:Win32/Amadey!rfn – A Stealthy Trojan Threat
Trojan:Win32/Amadey!rfn is a heuristic detection for a Trojan horse that exhibits malicious behavior capable of compromising sensitive user data, installing…
Bpant Ransomware: Understanding and Mitigating the Threat
If your files suddenly have the extension .Bpant and a ransom note demands Bitcoin payments, your system is likely infected…
Searchinstyle.com Browser Hijacker: Removal and Prevention
Searchinstyle.com is a browser hijacker and a potentially unwanted application (PUA) that infiltrates systems through bundled software installations or deceptive…
Trojan.MisplacedLegit.AutoIt Malware: A Detailed Guide to Understanding and Removal
Trojan.MisplacedLegit.AutoIt is a Trojan malware threat often linked to the misuse of the AutoIt scripting language, a legitimate tool for…
Disoaq App: Understanding the Threat and How to Remove It Safely
Potentially Unwanted Applications (PUAs) such as Disoaq App can have hazardous effects on systems and user privacy. This article delves…
D0glun Ransomware – Threat Analysis and Removal Guide
Ransomware continues to evolve, with new threats like D0glun targeting unsuspecting users. This ransomware-type virus encrypts victims' files and demands…
Removing InvisibleFerret Malware
InvisibleFerret is a Python-based backdoor malware associated with North Korean threat actors. It is a highly sophisticated tool used to…
Clone Ransomware: Understanding the Threat and How to Remove It Effectively
Clone ransomware is a member of the notorious Dharma ransomware family, identified during a routine analysis of malicious submissions on…
Chatsixgirl.com Redirect Virus: Detailed Removal Guide and Prevention Tips
Chatsixgirl.com is a harmful and deceptive website categorized as a potentially unwanted program (PUP). Though it may appear to offer…
Helldown Ransomware Removal
Helldown is an aggressive ransomware strain first identified in August 2024. It operates using double extortion tactics, encrypting victims’ data…
What Is Steam.aeonsecho.com?
Steam.aeonsecho.com is a deceptive website posing as a portal for an online adult game on Steam. It is designed to…
“Docker” Will Damage Your Computer Mac Virus
The “Docker” Will Damage Your Computer Mac virus is an annoying and potentially harmful software that targets Mac users. Though…
“Fine For Visiting Pornographic Websites” Scam
The "Fine For Visiting Pornographic Websites" scam is a deceptive scheme targeting unsuspecting users with fake fines for alleged law…
LightSpy Spyware: Understanding and Removing This Threat
LightSpy is a spyware-type program known for its data-stealing and spying activities. It has been active since at least 2020…
What is WebIntegration Adware?
WebIntegration is an adware application that displays intrusive ads and poses significant privacy and security risks. It belongs to the…
Trojan:BAT/Starter.G!Ink – What It Is, How to Remove It, and Prevention Tips
Trojan:BAT/Starter.G!Ink is a stealthy and highly dangerous malware that uses the Windows .BAT file format to execute administrative commands without…
AlrustiqApp.exe: A Trojan Threat
AlrustiqApp.exe is a dangerous Trojan horse malware designed to secretly mine cryptocurrency and exploit system resources. Beyond its mining capabilities,…
SyncUpgrade Adware: Understanding and Removing the Threat
The SyncUpgrade application is a deceptive program designed to disrupt users' browsing experiences through intrusive advertisements and possible data collection.…
InvisibleFerret Backdoor Malware: Understanding, Removing, and Preventing Future Infections
InvisibleFerret is a sophisticated Python-based backdoor malware associated with North Korean threat actors. This malicious program is primarily used for…
Protect Your iOS and macOS Devices from Smart Keystroke Recorder
Smart Keystroke Recorder is a commercial surveillance tool described as a keylogger. Designed to monitor and log user activity, it…
Setup.Exe Spyware/Malware/Trojan/Ransomware/Process
The “setup.exe” process is a commonly used file name for legitimate software installation. However, cybercriminals often exploit this name to…
Removing the Rotq App Threat
The Rotq App is a suspicious application flagged by multiple security vendors for its malicious behavior. Though it lacks clear…
BlackPanther Ransomware
BlackPanther is a dangerous ransomware strain that locks your files by encrypting them and demands payment for their decryption. Once…
Javct.net Pop-up Ads Virus
Javct.net is a potentially harmful browser hijacker and a source of disruptive pop-up ads and redirects. This article provides a…
Ezyplugin.com Mobile App Scam: Detailed Exposé, Removal Guide, and Prevention Methods
Ezyplugin.com is a fraudulent mobile app scam targeting iOS and Android users seeking hacked games, mods, coin generators, spoofing tools, and…
LulzDecryptor Ransomware: Threat Analysis, Removal, and Prevention
Understanding LulzDecryptor Ransomware The LulzDecryptor Ransomware is a file-locking Trojan designed to encrypt files on Windows systems, rendering them unusable.…
Understanding and Removing ProgressMapper Adware
ProgressMapper is a deceptive application categorized as adware. Its primary purpose is to generate intrusive advertisements that disrupt user experiences,…
How to Detect, Remove, and Prevent RecordTransaction Adware on Mac Devices
Adware remains a persistent threat to internet users, exploiting vulnerabilities to deliver intrusive advertisements and compromise user privacy. RecordTransaction is…
Hyena Ransomware: Analysis and Removal Guide
Hyena ransomware, a member of the MedusaLocker family, is a dangerous malware strain that encrypts files and demands payment for…
Enhancedefense[.]com Scam: What You Need to Know and How to Protect Yourself
Enhancedefensecom is a deceptive website that employs fake security alerts, pop-up ads, and intrusive notifications to manipulate users into interacting…
ProjectSet Adware: A Threat Overview and Removal Guide
The ProjectSet application, identified as part of the AdLoad malware family, is a deceptive adware program that jeopardizes the integrity…
WeRus Ransomware: Threat and Its Removal
Ransomware has become a significant menace in the digital world, with the WeRus ransomware standing out as a recent and…
Vulakingliter.com Browser Hijacker: Risks, Removal, and Prevention
Vulakingliter.com is a domain associated with the streaming platform Lookmovie.lol, which raises significant concerns regarding potential security risks. Visitors to…
Removing WantToCry Ransomware and Preventing Future Infections
Ransomware attacks are among the most destructive cyber threats faced by individuals and organizations. The WantToCry ransomware exemplifies this danger,…
Virus:Win32/Virut: Removal Guide
Virus:Win32/Virut is a highly dangerous trojan malware designed to infiltrate systems, steal sensitive data, and utilize resources for illicit activities…
opdomain22[.]online: Removal Guide & Prevention Tips
opdomain22online is a deceptive website designed to promote scams and expose users to potential malware threats. It lures unsuspecting users…
Mobitera[.]online: Detection, Removal, and Prevention
The internet is full of deceptive websites aiming to exploit users for financial gain or to infiltrate devices with harmful…
Xxxbf.com Adware: Understanding the Threat and Protecting Your Devices
Xxxbf.com is a type of adware that infiltrates devices to display intrusive ads, manipulate browsing behavior, and compromise user privacy.…
Fuq.com Browser Hijacker: Understanding, Removing, and Preventing This Threat
The Fuq.com browser hijacker is a pervasive security threat that infiltrates web browsers and disrupts the user's browsing experience. Found…
Hotbvigatu.cc: Understanding and Removing the Threat
Hotbvigatu.cc is a deceptive browser extension that operates as a Potentially Unwanted Program (PUP). While it may claim to enhance…