TeamCity On-Premises Vulnerability (CVE-2024-23917) Raises High-Stakes Concerns
A critical authentication bypass vulnerability, CVE-2024-23917, discovered in all versions of TeamCity On-Premises from 2017.1 through 2023.11.2 has triggered an…
Ov3r_Stealer Malware: A Deceptive Campaign Targeting Sensitive Information
In the ever-evolving landscape of cybersecurity threats, Ov3r_Stealer has emerged as a multifaceted malware designed to infiltrate and compromise systems,…
Farabuy.com Nuisance: A Comprehensive Guide to Eliminating Annoying Pop-ups
In the vast realm of online threats, the persistence of pop-up ads from sites like Farabuy.com has become a significant…
EdgeSimplePower.co.in: A Comprehensive Guide to Removing Annoying Pop-ups
EdgeSimplePower.co.in, with its persistent pop-up ads, has become a thorn in the side of users navigating the web. This article…
16691trULjLy1nscmMAJJi5bxULBUWBr9F Trojan: A Comprehensive Removal Guide
In recent times, a malicious Trojan known as 16691trULjLy1nscmMAJJi5bxULBUWBr9F has been making waves in the cyber threat landscape, posing a…
Rage Malware: A Stealthy Information Stealer
In the ever-evolving landscape of cyber threats, a particularly insidious player has emerged – Rage (also identified as RageStealer or…
Myhotfeed.com: A Browser Hijacker and Redirect Nuisance
Myhotfeed.com has emerged as a troublesome site known for orchestrating redirect loops and bombarding users with push notifications. Its presence…
Critical Vulnerability (CVE-2024-21893) Exploited: Ivanti Products at Risk
A critical server-side request forgery (SSRF) vulnerability, identified as CVE-2024-21893, has recently been exploited at an alarming scale in Ivanti…
Web Ads Filter: Safeguard Your Browsing Experience
If you've encountered issues related to Web Ads Filter while browsing, it's essential to address the problem promptly. This guide…
LookupToolDaemon on Mac: A Comprehensive Removal Guide
If you're facing the menace of LookupToolDaemon on your Mac, it's imperative to take swift action to eradicate this intrusive…
FadBlock: Understanding the Trojan Horse Threat
If you've noticed peculiar behavior on your computer, such as sluggishness, unresponsive applications, or unexpected warnings from your antivirus software,…
Onlypcflow.co.in: Battling the Browser Hijacker Onslaught
If you've found your web browser under the control of an unwelcome entity called Onlypcflow.co.in, your online experience is likely…
Networkpcigniter.com: A Rogue Webpage Exploiting Deceptive Content and Push Notification Spam
In the realm of cybersecurity, rogue webpages like networkpcigniter.com pose a significant threat to online users. Through deceptive content and…
Totalnicenewz.com – Navigating the Hazards of Rogue Webpages
In the ever-evolving landscape of online threats, rogue webpages like totalnicenewz.com have emerged as conduits for various cyber risks. Discovered…
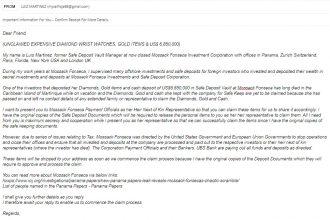
“Unclaimed Expensive Goods” Email Scam: A Deceptive Scheme Exploiting Mossack Fonseca Connection
In the realm of cyber threats, phishing scams persist as a prevalent danger, with attackers deploying cunning tactics to exploit…
“KYC (Know Your Customer) Verification” Email Scam: A Cryptocurrency Threat
In the ever-evolving landscape of cyber threats, scams targeting cryptocurrency users continue to rise. The "KYC (Know Your Customer) Verification"…
“BitDogs Mint Free” Scam: A Crypto-Draining Deception
In the dynamic world of cryptocurrencies and NFTs (Non-Fungible Tokens), scammers are employing sophisticated tactics to deceive users and drain…
MethodOnline: The Adware Intruder on Your Mac
In the ever-evolving landscape of cyber threats, adware continues to be a persistent menace. MethodOnline, a recent addition to the…
DataControl: Navigating the Adware Menace
In the realm of cybersecurity, threats evolve, and among them, advertising-supported applications like DataControl wield intrusive tactics. This article aims…
LPER Ransomware: A Menace from the STOP/Djvu Ransomware Lineage
Amidst the expansive landscape of cyber threats, LPER Ransomware emerges as a sinister iteration within the notorious STOP/Djvu Ransomware family.…
How Do I Deal with the ESSY Ransomware Infection?
ESSY Ransomware is yet another malware strain that is a part of the prolific STOP/Djvu Ransomware family. Like other similar…
TheHiddenObjectShow Adware on Mac: Unmasking the Threat
TheHiddenObjectShow has emerged as a potent adware threat targeting Mac users, causing a surge in intrusive pop-ups, unexpected redirects, and…
PixelMegabyte: Unwanted Adware on Your Mac
In the ever-evolving landscape of online threats, PixelMegabyte has emerged as a potential menace, classified as adware. This application raises…
PrivateLoader: Unveiling the Elusive Threat
In the perilous realm of cybersecurity, PrivateLoader stands out as a sophisticated and adaptable malware, categorized as a loader with…
VajraSpy Android Malware: A Threat to Your Privacy
In the ever-evolving landscape of cyber threats, VajraSpy stands out as a formidable adversary, specifically designed for targeted espionage on…
“VisionCoordinator Will Damage Your Computer” on Mac – Removal
Mac users encountering the threat of VisionCoordinator need to act promptly to safeguard their systems. This guide is tailored to…
CVE-2022-48618: Apple Flaw in macOS, iOS Actively Exploited
In a recent revelation, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified and added a high-severity flaw to…
UNC4990 Threat Group: Exploiting USB Devices and Legitimate Platforms
In a recent revelation, cybersecurity firm Mandiant has exposed the activities of a financially motivated threat actor known as UNC4990.…
Re-captha-version-3-21.icu Browser Hijacker: A Comprehensive Guide
The online realm, while brimming with opportunities and information, is not without its pitfalls. Enter Re-captha-version-3-21.icu, a bothersome browser hijacker…
1E3mVbLSLLUgdmrp8GV5RRu1Qz5FkWs4rJ Bitcoin Email Scam
In the vast landscape of cyber threats, the 1E3mVbLSLLUgdmrp8GV5RRu1Qz5FkWs4rJ Bitcoin email scam has emerged as a deceptive and intimidating scheme.…
“Yamaha Baby Grand Piano” Email Scam
In the realm of cyber threats, scammers often employ various tactics to trick unsuspecting individuals, and one such deceptive scheme…
“Claim Manta” Cryptocurrency Giveaway Scam
In the ever-evolving landscape of online scams, a new threat has emerged— the "Claim Manta" cryptocurrency giveaway scam. This deceptive…
Dx31 Ransomware: Unraveling the Threat and Protecting Your Data
In a recent inspection of malware samples submitted to VirusTotal, a new ransomware named Dx31 has been identified as part…
StandartSkill Adware: Unwanted Ads and Privacy Risks
StandartSkill, upon detailed examination, has been identified as adware, presenting users with intrusive advertisements and potential privacy risks. This article…
Unharmonious.app: Adware Threat Analysis and Removal Guide
Unharmonious.app has been identified as advertising-supported software (adware) belonging to the Pirrit malware family. Discovered during an investigation of new…
TypicalSource on Mac: Unveiling the Adware Threat
If your Mac is currently grappling with the threat of TypicalSource, swift action is imperative. This guide is tailored to…
SystemDesignMarket Mac Adware: Unveiling the Threat
For Mac users facing the intrusion of SystemDesignMarket, prompt action is imperative. This guide is meticulously crafted to aid users…
ExtendedOperation Adware on Mac: Unveiling the Threat
If you're facing the menace of ExtendedOperation on your Mac, swift action is imperative. This comprehensive guide is tailored to…
BounceTopics Adware: Unmasking the Threat
BounceTopics, identified as an adware-type application from the AdLoad malware family, poses a significant threat by delivering intrusive advertisement campaigns.…
RadioDiskInput Adware: Protecting Against Intrusive Ads
In recent investigations, cybersecurity experts have unveiled the RadioDiskInput application, operating as adware with the potential to compromise user information.…
AdjustableIndexer: Adware Lurking in the Shadows
The cybersecurity landscape continually evolves, and with it, the emergence of adware threatens the privacy and security of users. One…
“FTX Customer Claims” Scam: Protecting Your Cryptocurrency
In the vast realm of cyberspace, scammers are relentless in their pursuit of deceiving individuals and pilfering cryptocurrency. The "FTX…
ChallengeDiscovery: The Adware Onslaught
In the realm of cyber threats, ChallengeDiscovery has surfaced as a new adversary, revealing its identity as adware within the…
QuestDevice: Adware Intrusion on Mac
QuestDevice has emerged as a problematic application, marked by its intrusive advertisement tactics, classifying it as adware. Beyond bombarding users…
Browser Default: A Browser-Hijacking Nuisance on Mac
Browser Default, a potentially unwanted add-on infiltrating popular browsers such as Safari, Firefox, and Chrome, disrupts user experience by altering…
Notifzone.com: A Push Notification Peril
Have you encountered the vexing Notifzone.com and its persistent push notifications, inducing redirect loops? This article delves into the dubious…
FindItQuickSearch.com: A Browser Hijacker’s Intrusion
Are you tired of the disruptions caused by FindItQuickSearch.com in your browser? This article is designed to guide you through…
Superquicksearch.com Browser Hijacker: Unraveling the Intrusion
If you find Superquicksearch.com disrupting your browsing experience, it's time to take decisive action. This guide is tailored to assist…
PowerRemote on Mac: Unveiling the Adware Intrusion
If your Mac is grappling with the presence of PowerRemote, immediate action is imperative. This adware, associated with the notorious…
CrossSighnfld on Mac: Battling the Adware Onslaught
If your Mac is under the threat of CrossSighnfld, immediate action is vital. This guide is meticulously crafted to help…