PlayBoy LOCKER Ransomware: Comprehensive Removal and Prevention Guide
PlayBoy LOCKER is a highly dangerous ransomware that encrypts your files and demands payment in exchange for their decryption. This…
Cloak Ransomware: A Comprehensive Analysis and Removal Guide
Cloak ransomware is a malicious software that encrypts files on infected systems and demands a ransom for decryption. Emerging between…
CmbLabs Ransomware: A Comprehensive Threat Analysis and Removal Guide
CmbLabs ransomware is a newly discovered malware strain designed to encrypt files and demand payment for decryption. This ransomware was…
.V Virus File (Dharma Ransomware) Removal Guide
Dharma ransomware has long been one of the most persistent ransomware families, and the latest variant, known as .V Virus…
Core (Makop) Ransomware: A Guide to Removal and Prevention
Ransomware remains one of the most persistent and damaging cyber threats. One of the latest strains identified is Core (Makop)…
V (Dharma) Ransomware: Analysis and Removal Guide
Understanding V (Dharma) Ransomware V is a ransomware variant belonging to the notorious Dharma family, a well-known group of ransomware…
LCRYPTX Ransomware: A Comprehensive Threat Analysis and Removal Guide
LCRYPTX is a ransomware-type malware that encrypts victims' files and demands a ransom for decryption. This cyber threat was recently…
BlackLock Ransomware: A Analysis and Removal Guide
BlackLock is a ransomware-type virus that encrypts files and demands ransoms for decryption. It renames encrypted files with a random…
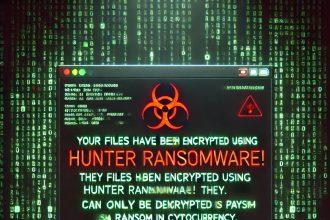
Hunter Ransomware: A New Variant of Prince Ransomware – Removal & Prevention Guide
A new ransomware threat named Hunter has emerged, encrypting victims’ files and demanding payment in cryptocurrency for decryption. Hunter ransomware…
SpiderParadise Ransomware: Analysis and Removal Guide
Ransomware is one of the most dangerous types of malware, locking victims out of their files and demanding a ransom…
Revenge Of Heisenberg Ransomware
Overview of Revenge Of Heisenberg Ransomware Revenge Of Heisenberg is a ransomware strain based on the Chaos ransomware family. This…
Hitler_77777 Ransomware: Analysis and Removal Guide
The Hitler_77777 ransomware is a dangerous cryptovirus identical to TRUST FILES ransomware. This malicious software encrypts victims’ files and modifies…
REDKAW Ransomware: A New Data-Encrypting Threat Demanding Ransom
Understanding REDKAW Ransomware REDKAW is a newly discovered ransomware variant designed to encrypt victims’ files and demand payment for decryption.…
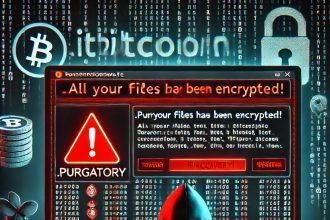
Purgatory Ransomware: Threat Analysis and Removal Guide
Purgatory ransomware is a malicious program that encrypts files on infected systems and demands payment for decryption. This threat has…
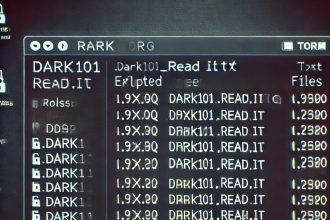
Dark 101 Ransomware: A Detailed Threat Analysis and Removal Guide
Dark 101 is a ransomware-type malware based on the Chaos framework, recently discovered during a routine inspection of new submissions…
Mania Crypter Ransomware: Understanding and Removing the Threat
Mania Crypter is a dangerous ransomware variant based on the infamous LockBit Black. This malware encrypts files, appends a random…
innok Ransomware: Analyzing the Threat and How to Remove It
Ransomware remains one of the most pervasive cyber threats, and innok ransomware is no exception. This malicious software encrypts victims’…
EByte Locker Ransomware: A Detailed Guide to Understanding, Removing, and Preventing This Threat
What Is EByte Locker Ransomware? EByte Locker is a malicious ransomware strain based on the Prince ransomware family. It encrypts…
Spring Ransomware: Understanding and Removal
Spring ransomware is a malicious program based on the CONTI ransomware family, designed to encrypt files and demand a ransom…
Protect Your Cryptocurrency: Jupiverse Wallet Connection Scam Exposed
The world of cryptocurrency has brought immense opportunities, but it also opens doors to sophisticated scams. One such alarming threat…
Bpant Ransomware: Understanding and Mitigating the Threat
If your files suddenly have the extension .Bpant and a ransom note demands Bitcoin payments, your system is likely infected…
D0glun Ransomware – Threat Analysis and Removal Guide
Ransomware continues to evolve, with new threats like D0glun targeting unsuspecting users. This ransomware-type virus encrypts victims' files and demands…
Clone Ransomware: Understanding the Threat and How to Remove It Effectively
Clone ransomware is a member of the notorious Dharma ransomware family, identified during a routine analysis of malicious submissions on…
Helldown Ransomware Removal
Helldown is an aggressive ransomware strain first identified in August 2024. It operates using double extortion tactics, encrypting victims’ data…
BlackPanther Ransomware
BlackPanther is a dangerous ransomware strain that locks your files by encrypting them and demands payment for their decryption. Once…
LulzDecryptor Ransomware: Threat Analysis, Removal, and Prevention
Understanding LulzDecryptor Ransomware The LulzDecryptor Ransomware is a file-locking Trojan designed to encrypt files on Windows systems, rendering them unusable.…
Hyena Ransomware: Analysis and Removal Guide
Hyena ransomware, a member of the MedusaLocker family, is a dangerous malware strain that encrypts files and demands payment for…
WeRus Ransomware: Threat and Its Removal
Ransomware has become a significant menace in the digital world, with the WeRus ransomware standing out as a recent and…
Removing WantToCry Ransomware and Preventing Future Infections
Ransomware attacks are among the most destructive cyber threats faced by individuals and organizations. The WantToCry ransomware exemplifies this danger,…
Annoy Ransomware: Comprehensive Removal Guide & Prevention Tips
Have your files been locked by the Annoy Ransomware virus? This insidious ransomware encrypts files and demands payment in cryptocurrency…
Nnice Ransomware: Analysis and Removal Guide
Nnice ransomware is a malicious program designed to encrypt files and extort victims by demanding payment for file decryption. This…
Darkadventurer Ransomware
The Darkadventurer Ransomware is a dangerous form of malicious software that encrypts various file types on infected systems, rendering them…
SAGE 2.2 Ransomware: A Comprehensive Guide
SAGE 2.2 is a dangerous strain of ransomware that belongs to the crypto virus family, notorious for encrypting files and…
An In-Depth Look at Anomaly Ransomware: How to Protect Yourself
Anomaly ransomware, a dangerous variant based on the Chaos ransomware family, has emerged as a significant threat to computer users…
LucKY_Gh0$t Ransomware: Understanding and Removing the Threat
LucKY_Gh0$t is a dangerous ransomware strain that has recently been gaining attention for its sophisticated encryption techniques and its ties…
Aptlock Ransomware: A Threat Analysis and Removal Guide
Ransomware attacks continue to pose significant threats to businesses and individuals, with Aptlock being a recent and alarming addition to…
How to Deal with FunkLocker (FunkSec) Ransomware?
FunkLocker, also known as FunkSec, is a dangerous and highly disruptive type of ransomware that encrypts your files and demands…
Contacto Ransomware: A Detailed Overview and Removal Guide
Contacto ransomware is a malicious program that encrypts users’ files and demands a ransom for their decryption. This ransomware has…
YE1337 Ransomware: A Detailed Guide to Detection, Removal, and Prevention
Ransomware attacks have become one of the most significant threats to digital security, impacting individuals and businesses alike. One such…
Nitrogen Ransomware: Removal and Prevention
Nitrogen ransomware is a malicious software designed to encrypt files on infected systems, rendering them inaccessible without a decryption key.…
Bbuild Ransomware: Understanding, Removal, and Prevention
Ransomware remains one of the most destructive and costly cyber threats today, and one such notorious strain is Bbuild. Discovered…
RdpLocker Ransomware: Understanding, Removing, and Preventing Future Infections
RdpLocker is a sophisticated form of ransomware that targets personal and business data by encrypting files and demanding a ransom…
Held Ransomware Removal
Ransomware attacks continue to pose significant threats to individuals and organizations worldwide. One of the latest variants in the Djvu…
Kixtixcy Ransomware: Understanding and Removing the Threat
Ransomware continues to be a prominent and devastating form of cyberattack, with Kixtixcy ransomware—a member of the notorious Dharma family—emerging…
Vulcan Ransomware: A Guide to Understanding and Removing This Threat
Ransomware attacks are among the most alarming forms of cybercrime, and Vulcan ransomware is the latest addition to this malicious…
.Held Ransomware: A Comprehensive Guide to Removal and Prevention
The infamous DJVU ransomware family has resurfaced with a new variant just in time for the 2024 holiday season: the…
What Is Teaneck.exe Trojan Malware and How to Remove It
Trojan malware, named after the deceptive Trojan horse of Greek mythology, is one of the most insidious types of cyber…
Dark Intel Ransomware: Detection, Removal, and Prevention
Introduction to Dark Intel Ransomware Dark Intel is a ransomware strain recently identified during the analysis of malicious file samples…
MRJOKERPALFINGER1984 Ransomware: A Detailed Analysis and Removal Guide
Understanding the MRJOKERPALFINGER1984 Ransomware Threat MRJOKERPALFINGER1984 is a ransomware variant designed to encrypt victims' files and extort a hefty ransom…
AlienWare Ransomware: A Understanding and Removing the Threat
Ransomware has become one of the most devastating forms of malware in the digital landscape, targeting personal and corporate data…