CommonMethod Adware: A Dangerous AdLoad Malware Variant
CommonMethod is a form of adware that belongs to the notorious AdLoad malware family. Discovered during a security investigation of…
TechBoost Adware: A Security Threat You Should Remove Immediately
TechBoost is classified as adware that primarily targets Mac users. It bombards users with intrusive advertisements, exposes them to scams,…
Tiny FUD Trojan: A Dangerous macOS Threat and How to Remove It
Tiny FUD is a highly sophisticated Trojan targeting macOS users. The term FUD (Fully Undetectable) suggests that this malware is…
OneBrowser Virus – Complete Removal Guide
What Is OneBrowser? OneBrowser is a deceptive and potentially unwanted program (PUP) that functions as a fake web browser. Instead…
Suaiqi App – A Potentially Unwanted Application (PUA) Spreading Legion Loader Malware
The Suaiqi App is a Potentially Unwanted Application (PUA) that has been discovered within an installer distributed via rogue websites.…
Core (Makop) Ransomware: A Guide to Removal and Prevention
Ransomware remains one of the most persistent and damaging cyber threats. One of the latest strains identified is Core (Makop)…
V (Dharma) Ransomware: Analysis and Removal Guide
Understanding V (Dharma) Ransomware V is a ransomware variant belonging to the notorious Dharma family, a well-known group of ransomware…
Altruistics Virus: A Dangerous Cryptojacking Trojan – Removal Guide and Prevention Tips
The Altruistics virus is a type of Trojan horse malware that infiltrates computers by disguising itself as legitimate software or…
BlackMoon Banking Trojan: A Dangerous Threat to Financial Security
BlackMoon, also known as KrBanker, is a banking Trojan that has been targeting online banking users since 2014. This malware…
Destiny Stealer Malware: A Dangerous Threat to Your Online Security
Cybercriminals continuously develop and distribute new threats that put users’ sensitive information at risk. One such advanced malware is Destiny…
LCRYPTX Ransomware: A Comprehensive Threat Analysis and Removal Guide
LCRYPTX is a ransomware-type malware that encrypts victims' files and demands a ransom for decryption. This cyber threat was recently…
CommonBoost Adware: A Complete Removal Guide and Prevention Tips
CommonBoost is an adware application that bombards users with intrusive advertisements, which can lead to scams and various cybersecurity risks.…
BlackLock Ransomware: A Analysis and Removal Guide
BlackLock is a ransomware-type virus that encrypts files and demands ransoms for decryption. It renames encrypted files with a random…
Totraxilly.co.in Pop-up Virus – How to Remove It and Stay Protected
Totraxilly.co.in is a deceptive website that tricks users into allowing intrusive notifications, leading to excessive pop-ups and redirections to dangerous…
FastFix Mac Adware (PUP) – Removal Guide & Prevention Methods
What is FastFix? FastFix is a Potentially Unwanted Program (PUP) and adware that primarily targets Mac users. It is a…
Coyote Banking Trojan: A Growing Threat to Online Financial Security
Cybersecurity experts at FortiGuard Labs have recently identified a new malware campaign using malicious Windows Shortcut (LNK) files to spread…
Localswithsecrets.com Pop-up Ads Virus – Removal Guide and Prevention Tips
Localswithsecrets.com is a misleading online platform that disguises itself as a legitimate dating website but actually serves as a browser…
Pentagon Malware: A Comprehensive Guide to Detection, Removal, and Prevention
The rise of cyber threats continues to endanger personal and corporate security. One such malicious entity is Pentagon malware, a…
OriginalAccessibility Adware: A Threat to Mac Users and How to Remove It
OriginalAccessibility is an adware program that primarily targets Mac computers. It belongs to the notorious Adload malware family, known for…
OtterCookie Malware: A Comprehensive Guide to Detection, Removal, and Prevention
OtterCookie is a sophisticated piece of malware designed primarily for information theft, with a specific focus on cryptocurrency wallets. This…
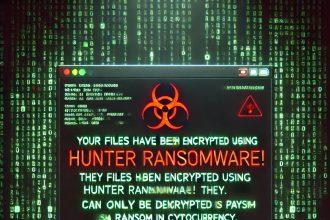
Hunter Ransomware: A New Variant of Prince Ransomware – Removal & Prevention Guide
A new ransomware threat named Hunter has emerged, encrypting victims’ files and demanding payment in cryptocurrency for decryption. Hunter ransomware…
SpiderParadise Ransomware: Analysis and Removal Guide
Ransomware is one of the most dangerous types of malware, locking victims out of their files and demanding a ransom…
Searchsqout.com Browser Hijacker – Comprehensive Removal Guide
Searchsqout.com is a deceptive website classified as a browser hijacker and potentially unwanted program (PUP). It infiltrates users’ browsers through…
PDF2DOCS.com Browser Hijacker: Threat Analysis & Removal Guide
Overview of PDF2DOCS.com PDF2DOCS.com is a misleading website that claims to provide users with an easy-to-use PDF to Microsoft Word…
Revenge Of Heisenberg Ransomware
Overview of Revenge Of Heisenberg Ransomware Revenge Of Heisenberg is a ransomware strain based on the Chaos ransomware family. This…
FastFix Adware: Removal and Prevention
FastFix is an adware application that exhibits intrusive behavior by generating unwanted advertisements and tracking user activity. This adware, which…
Hitler_77777 Ransomware: Analysis and Removal Guide
The Hitler_77777 ransomware is a dangerous cryptovirus identical to TRUST FILES ransomware. This malicious software encrypts victims’ files and modifies…
REDKAW Ransomware: A New Data-Encrypting Threat Demanding Ransom
Understanding REDKAW Ransomware REDKAW is a newly discovered ransomware variant designed to encrypt victims’ files and demand payment for decryption.…
Login Tab – Faster Access to Favorite Sites Browser Hijacker: A Cybersecurity Threat Analysis and Removal Guide
The "Login Tab - Faster access to favorite sites" is a browser hijacker that modifies browser settings to promote the…
EpiStart (EpiBrowser) – A Rogue Browser That Threatens Your Online Security
EpiStart, also known as EpiBrowser, is a rogue web browser built on the Chromium open-source project. While it may seem…
TorNet Malware: A Dangerous Backdoor Threat and How to Remove It
TorNet is a highly dangerous backdoor malware designed to infiltrate computer systems, establish persistent access, and enable further infections. This…
Trojan:Win32/Phonzy.A!ml Malware Removal
Trojan:Win32/Phonzy.A!ml is a highly dangerous malware designed to infect systems by acting as a loader for additional threats. It can…
SeekThatOnline – Access to Favorite Sites Browser Hijacker: Removal Guide & Prevention
The SeekThatOnline - Access to Favorite Sites browser hijacker is a deceptive program that modifies browser settings to promote the…
Trojan:Win32/Cloxer Malware – Detection, Removal, and Prevention
Trojan:Win32/Cloxer is a highly dangerous Trojan horse malware that acts as a loader to install additional threats on infected systems.…
Miboxpixorerealpath[.]com
Miboxpixorerealpath.com is a rogue website known for promoting deceptive content, intrusive browser notifications, and redirecting users to potentially malicious sites.…
Search-globe.com Browser Hijacker
Protecting your device from intrusive and untrustworthy Potentially Unwanted Programs (PUPs) is essential for maintaining a secure online experience. One…
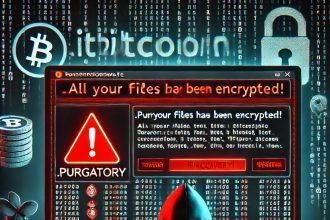
Purgatory Ransomware: Threat Analysis and Removal Guide
Purgatory ransomware is a malicious program that encrypts files on infected systems and demands payment for decryption. This threat has…
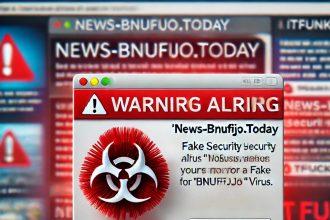
News-bnufijo.today Pop-up Virus – Complete Removal Guide
What Is News-bnufijo.today? News-bnufijo.today is a browser hijacker and potentially unwanted program (PUP) that aggressively redirects users to suspicious websites,…
Hotbsopika.cc: A Dangerous Browser Hijacker and How to Remove It
Hotbsopika.cc is a malicious website that poses a significant threat to users by hijacking browsers, displaying intrusive advertisements, and redirecting…
“Safety Warning” Scam
Online scams are becoming increasingly sophisticated, preying on users' fears to manipulate them into falling for fraudulent schemes. One such…
Dark 101 Ransomware: A Detailed Threat Analysis and Removal Guide
Dark 101 is a ransomware-type malware based on the Chaos framework, recently discovered during a routine inspection of new submissions…
ClickFix Malware: Understanding and Removing the Threat
ClickFix is a deceptive malware campaign that tricks users into executing malicious commands under the guise of resolving errors or…
CatLogs Malware: Analysis and Removal Guide
CatLogs is a sophisticated stealer-type malware that has been creating significant havoc in the cybersecurity space. This malicious program is…
Bigsupersweepstakes.com: A Guide to Understanding and Eliminating the Threat
In the vast digital landscape, malicious entities like Bigsupersweepstakes.com emerge to exploit unsuspecting users. This rogue website employs manipulative tactics,…
Bright_setup.exe: Understanding the Threat and Removal Guide
Bright_setup.exe is a file associated with Bright VPN, a free virtual private network service provided by Bright Data. While Bright…
Networkcontrol.co[.]in Ads: Analysis and Removal
In today’s digital landscape, online threats are evolving, targeting unsuspecting users through various techniques. Networkcontrol.coin is one such deceptive page…
Mania Crypter Ransomware: Understanding and Removing the Threat
Mania Crypter is a dangerous ransomware variant based on the infamous LockBit Black. This malware encrypts files, appends a random…
Kowi SApp Threat Removal
What is Kowi SApp? Kowi SApp is a dangerous and unwanted application flagged by multiple security vendors. Deceptively distributed, it…
innok Ransomware: Analyzing the Threat and How to Remove It
Ransomware remains one of the most pervasive cyber threats, and innok ransomware is no exception. This malicious software encrypts victims’…
Cash-searcher[.]com
Cash-searchercom is a deceptive website designed to manipulate users into subscribing to its notifications or engaging with fraudulent schemes. Threat…