Core (Makop) Ransomware: A Guide to Removal and Prevention
Ransomware remains one of the most persistent and damaging cyber threats. One…
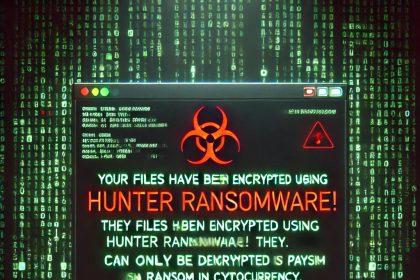
Hunter Ransomware: A New Variant of Prince Ransomware – Removal & Prevention Guide
A new ransomware threat named Hunter has emerged, encrypting victims’ files and…
Hitler_77777 Ransomware: Analysis and Removal Guide
The Hitler_77777 ransomware is a dangerous cryptovirus identical to TRUST FILES ransomware.…
Mania Crypter Ransomware: Understanding and Removing the Threat
Mania Crypter is a dangerous ransomware variant based on the infamous LockBit…
Removing WantToCry Ransomware and Preventing Future Infections
Ransomware attacks are among the most destructive cyber threats faced by individuals…
SAGE 2.2 Ransomware: A Comprehensive Guide
SAGE 2.2 is a dangerous strain of ransomware that belongs to the…
Held Ransomware Removal
Ransomware attacks continue to pose significant threats to individuals and organizations worldwide.…
Kixtixcy Ransomware: Understanding and Removing the Threat
Ransomware continues to be a prominent and devastating form of cyberattack, with…
.Held Ransomware: A Comprehensive Guide to Removal and Prevention
The infamous DJVU ransomware family has resurfaced with a new variant just…
Dark Intel Ransomware: Detection, Removal, and Prevention
Introduction to Dark Intel Ransomware Dark Intel is a ransomware strain recently…